Understanding Cloudflare Errors 1006, 1007, and 1008: Causes and Fixes
Cloudflare helps a big chunk of the internet run faster and stay safer by routing traffic through its worldwide network. But sometimes things don’t go smoothly, and you might see errors like 1006, 1007, or 1008. They all mean your request got blocked, but for different reasons. Let’s break down what each of these errors actually means.
Vaidotas Juknys
Last updated: Aug 04, 2025
6 min read
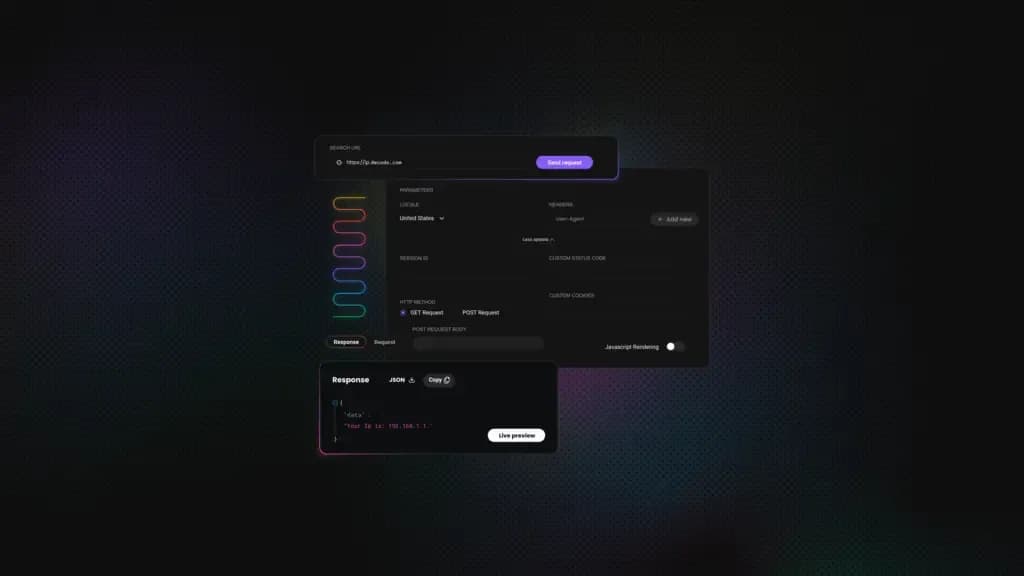
What are Cloudflare errors 1006, 1007, and 1008?
Cloudflare operates between visitors and a website's origin server, acting as a content‑delivery network but also as a security shield. It accelerates page loads by caching content and defends sites against denial‑of‑service attacks, bot traffic, and suspicious behaviour. Cloudflare's reverse‑proxy service powers nearly one‑fifth of all websites, and the company processes tens of millions of HTTP requests every second.
When something goes wrong, Cloudflare returns 1xxx error codes to tell you what is happening. Errors 1006, 1007, and 1008 are among the most common. All of them refused to pass your request to the origin. It can frustrate legitimate visitors, halt scraping projects, and even cut off site owners from their own dashboards, so understanding them is important.
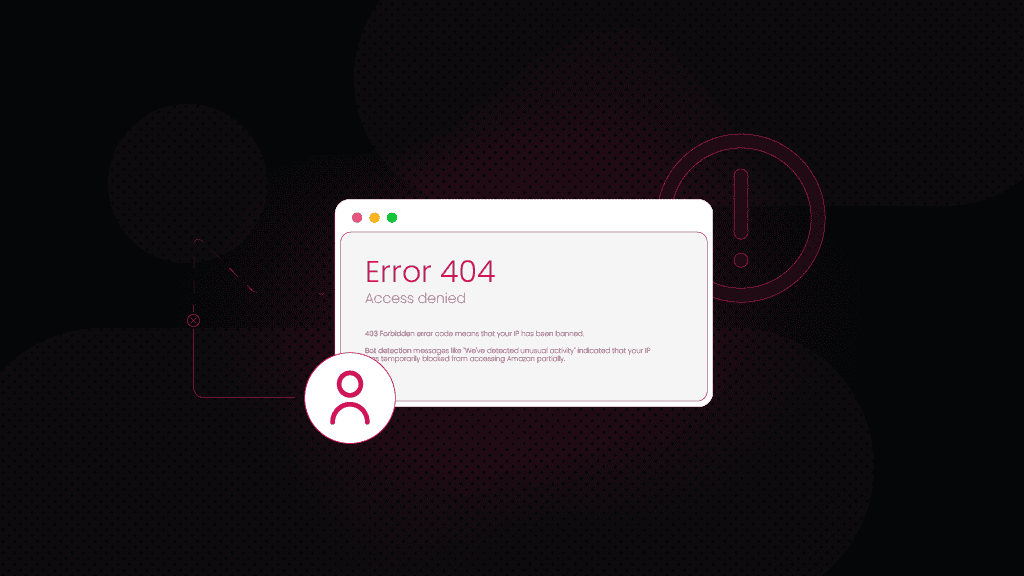
Error 1006: access denied due to IP ban
The most frequent error is 1006, which means that Cloudflare has blocked your current IP address. It's a catch‑all code that covers IP bans for many reasons, including:
- Suspicious activity
- Repeated failed requests
- Automated activities
You might encounter this ban if you or your team are scraping data too quickly, using a generic automation tool, or connecting through a poorly configured proxy. For regular visitors, it could be caused by a shared office IP that someone else abused. For web scrapers, this code is a clear sign that Cloudflare understood that you're running an automated data collection solution and it's time to adjust your scraping tool.
Error 1007: access denied due to IP or region restrictions
Error 1007 looks almost identical but signals something more specific. It appears when Cloudflare blocks your IP or network because of geographic restrictions or a manual IP‑range ban by the website owner. Some sites choose to block entire countries to comply with local regulations or to minimise abuse. If you're in a country that is blocked, you'll see an error 1007 message even if you haven't done anything wrong.
Error 1008: access denied by firewall or custom rules
Error 1008 indicates that your request violated a custom rule in the site's firewall. Cloudflare allows site owners to create granular Web Application Firewall (WAF) rules to block unwanted patterns, like specific user‑agent strings, referrers, query parameters or IP ranges. When your request triggers one of those rules, Cloudflare returns error 1008.
This might happen if you send unusual headers, use a rare HTTP method, or unwillingly match a pattern associated with known attacks. The 1008 one is less common than error 1006 and related to automation because sophisticated anti‑bot systems often rely on custom rules.
Why do these errors happen?
Cloudflare uses several ways to differentiate between human users and bots. Cloudflare's detection mechanisms contains:
- IP analysis and automatic bans based on known bad actors, rate excessive patterns or shared proxy pools.
- Geographic restrictions blocking IPs from specific countries or ASNs set by site rules.
- Firewall or security‑rule violations requests blocked when hitting custom WAF patterns, such as odd headers or blacklisted paths.
- Detection of suspicious or bot‑like behavior via TLS handshake fingerprinting and JS challenges.
Cloudflare checks the TLS handshake, things like cipher suite order and protocol version, to create a unique "fingerprint". The TLS fingerprints are compared to known browser profiles to identify automation frameworks. It may also deploy JavaScript puzzles or CAPTCHAs on the client side. If the browser can't run these or fails the test, Cloudflare tags it as a bot. Incoming IPs are checked against reputation databases where Cloudflare stores blocked addresses with a history of spam, scraping or DDoS activity. If the IP belongs to a blocked region or violates firewall policies, the access‑denied response will be returned. All these layers working together ensure that only legitimate human-like traffic gains access.
Common reasons you see errors 1006, 1007, and 1008
Let's understand why Cloudflare might block your request. Some reasons are technical, while others relate to how you or the website owner have configured things.
- High‑volume scraping or bot‑like patterns. Automation often sends many requests in quick succession. If your scraper doesn't mimic human browsing patterns, Cloudflare may interpret this as a distributed denial‑of‑service(DDoS) attack and return an access‑denied code.
- Poorly configured proxies. Free or unreliable proxy services often share IPs that have been abused by other users. These addresses may already be on Cloudflare's blacklist, triggering error 1006 or error 1007 immediately.
- Generic user agents or missing headers. Requests that do not include typical browser headers look suspicious. Some site owners create WAF rules to block such requests, leading to error 1008.
- Geographic blocks. To limit fraud or reduce compliance risk, websites can block traffic from specific countries. If you're connecting from a banned region or through an IP range associated with that region, you'll see error 1007.
- Custom firewall rules. A site owner might set up rules to block specific referrers, query parameters or user‑agents. If your request matches one of these rules, intentionally or inadvertently, Cloudflare responds with error 1008.
- DNS misconfiguration. Sometimes error 1006 is the result of an outdated or misconfigured DNS record. If your system resolves the domain to an incorrect IP address, Cloudflare can't forward your request and returns an access‑denied message.
Troubleshooting and fixes for website visitors
You can resolve most of the Cloudflare errors with just a few easy steps:
- Clear browser cache and cookies. Sometimes, stale browser data can cause Cloudflare to misinterpret your request. Clearing your cache and cookies forces your browser to fetch fresh content and can resolve minor conflicts.
- Check DNS settings. Try changing your DNS resolver to a public service such as 1.1.1.1 or 8.8.8.8. Flushing your local DNS cache afterwards ensures your system uses the new settings.
- Contact website owner. Cloudflare can't override a website owner's firewall rules. If none of the fixes work, check the "Contact" or "About" page and contact the site administrator. Explain that you're being blocked and provide your IP address.
- Use a different network, VPN or a proxy. If you suspect your IP has been blocked because of suspicious patterns or because you're connecting from a shared network, try using a different connection or resetting your IP address. Switching to a mobile hotspot, restarting your router or connecting via a trustworthy proxy or VPN often bypasses the block. For region‑based restrictions, choose a proxy server in an allowed country to avoid error 1007.
Troubleshooting and fixes for website owners and admins
When your site is protected by Cloudflare, encountering error 1006, 1007 or 1008 can lock out real human visitors. It's ruining the user experience and you're losing revenue with every restricted access. As a site administrator, you've got several backend tools to identify what's blocking access, adjust settings and restore access. Follow those tasks to resolve and prevent access blocks:
- Reviewing and adjusting Cloudflare firewall rules. In the firewall events section, you can filter by ray ID or rule ID to find the exact block event. Check if the rule is overly broad or misconfigured. If the rule is causing the block, tweak or disable it so real users aren't affected.
- Checking and modifying security levels. If the "I'm Under Attack" mode or DDoS protection is too strict, it can issue false positives. Lower the sensitivity or switch it off when no real attack is in progress.
- Whitelisting legitimate IPs. Add known‑good IPs via the IP Access rules page. The "Allow" action bypasses most Cloudflare checks, including security challenges and WAF rules.
- Reviewing WAF logs for false positives. Use event analytics or logpush data to see how often a rule blocks traffic. Frequent false positives suggest the rule should be rebalanced or moved to a "log only" mode rather than a block.
- Disabling or adjusting "Under Attack" mode or custom rules. If a custom rule or global setting is set to "block" or "challenge" unnecessarily, it may trigger error 1008. Temporarily disable it, switch to "challenge" or add an exception until you confirm what legitimate traffic is triggering it.
- Resolving DNS misconfigurations. Sometimes Cloudflare returns an access‑denied error because the DNS record is pointing to the wrong origin or is out‑of‑date. Check your DNS entries and switch to public resolvers like 1.1.1.1 or 8.8.8.8.
Residential proxies with #1 response time
Bypass CAPTCHAs, IP bans, and geo-restrictions with residential proxies. Start your 3-day free trial with 100MB today.
Best practices for developers
When collecting data from websites protected by Cloudflare, you must build your scraper to act like a regular internet user. Taking shortcuts will almost certainly result in an access‑denied error. Follow these guidelines to reduce the chance of triggering errors 1006, 1007, or 1008.
Use high‑quality proxies
Scraping from a single IP address is a red flag for any anti‑bot system. Residential and mobile proxies rotate your requests through IPs assigned to real devices, making your traffic look more legitimate. Choose a reliable proxy provider with a large, clean IP pool and avoid free proxy lists that are easily flagged. Rotate your IP regularly and distribute requests across many locations to avoid exhausting any one address. If you need to scrape sites that block certain countries, make sure you choose proxies in allowed regions to avoid error 1007.
Vary your user‑agent strings and headers
HTTP headers tell servers what type of client is making the request. Many scrapers forget to set realistic headers, leaving default values like "Python‑requests" or "curl/7.64.1." It's clearly used by a bot. Build a list of modern browser user-agents and rotate them across sessions. Include Accept, Accept‑Language and Accept‑Encoding headers to mimic real browsers. Changing your headers also helps avoid error 1008 because custom firewall rules often target specific header patterns.
Emulate human interaction patterns
Bots fail when they act too quickly or predictably. Add random delays between requests, follow logical navigation flows, and interact with elements on other pages that you can normally ignore. Wait for a few seconds when a page is loaded or scroll through a page like a normal user.
Leveraging advanced libraries
Use headless browser libraries such as Playwright or Puppeteer to execute JavaScript and render pages fully. These tools create a browser context that acts like a human while browsing, helping you pass JavaScript fingerprinting.
In addition to headless browser libraries, using a cloud phone allows developers to run scraping and automation tasks inside real mobile environments hosted in the cloud, reducing fingerprint inconsistencies and improving reliability when interacting with Cloudflare-protected websites.
Ethical considerations
While it's legal to collect publicly available data, it's important to do it ethically and legally. Here are a few tips:
- Always take a quick look at a site’s robots.txt file to see what you’re allowed to crawl.
- Make sure to read and follow the terms of service.
- When in doubt about data collection practices or a specific use case, it's best to consult with legal professional.
Playing fair helps you avoid getting blocked and helps you comply with the local and international laws.
Bottom line
Cloudflare errors 1006, 1007, and 1008 can be annoying, but they're here for a reason. Each code gives specific information about why your request was blocked no matter if it's a general IP ban, a region‑based restriction or a custom firewall rule. Visitors can simply deal with it by clearing their cache, switching networks, or contacting the site owner, which often solves the problem. Administrators can reduce false positives by reviewing firewall logs, adjusting security levels, and whitelisting legitimate IPs.
Developers need to take it a step further by using high-quality rotating proxies, varying user agents, emulating human behavior, and monitoring feedback. With careful planning and respect for website policies, you can prevent these errors and build more reliable data‑collection pipelines.
Avoid restrictions with residential proxies
Leave CAPTCHAs and IP bans behind – get started with a 3-day free trial.
About the author

Vaidotas Juknys
Head of Commerce
Vaidotas Juknys is a seasoned commercial leader with over a decade of experience spanning technology, telecommunications, and management consulting. Currently working as Head of Commerce, Vaidotas brings valuable insights from his diverse background in the technology industry and analytical expertize.
Connect with Vaidotas via LinkedIn.
All information on Decodo Blog is provided on an as is basis and for informational purposes only. We make no representation and disclaim all liability with respect to your use of any information contained on Decodo Blog or any third-party websites that may belinked therein.