Google Disrupts World's Largest Residential Proxy Network: Why Ethical IP Sourcing Matters
Google Threat Intelligence Group, together with Cloudflare, Spur, and Lumen's Black Lotus Labs, announced that it dismantled IPIDEA, one of the world's largest residential proxy networks, reducing available devices for proxy operators by millions. The network facilitated espionage operations, cybercrime, and botnet attacks while hijacking consumer bandwidth without proper consent. In a single 7-day period in January, over 550 individual threat groups from China, DPRK, Iran, and Russia used IPIDEA infrastructure to mask malicious activities. This disruption highlights a critical but often overlooked risk in digital operations. How companies source IP addresses and proxy services directly impacts security posture, regulatory compliance, and ethical standing in an increasingly scrutinized digital landscape.
Benediktas Kazlauskas
Last updated: Jan 29, 2026
8 min read
The hidden dangers of unethical IP sourcing
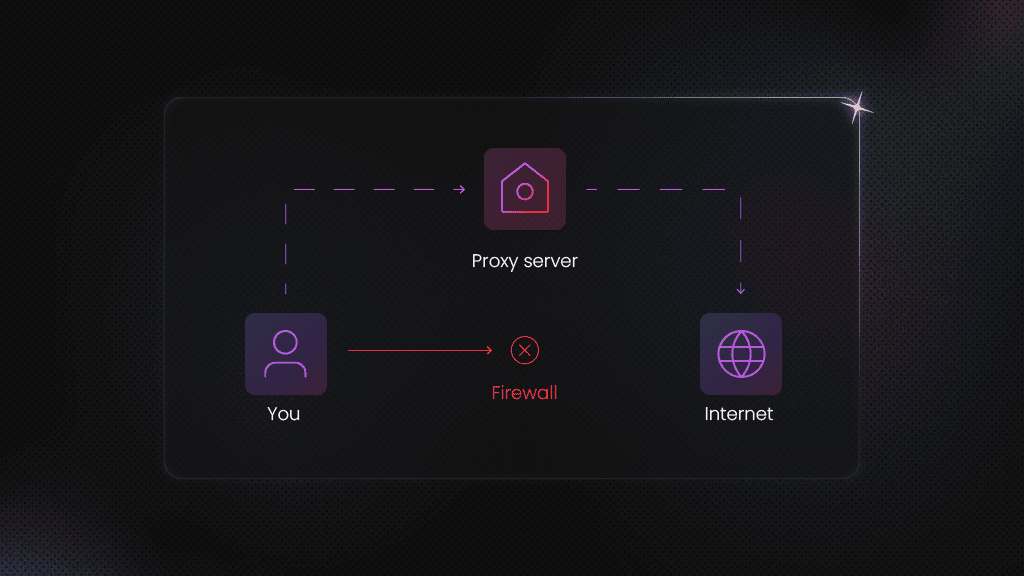
Residential proxy networks sell access to IPs owned by internet service providers and assigned to consumer devices. Unlike datacenter proxies, residential proxies route traffic through real consumer devices, making malicious activity harder to detect and block. This capability makes them a go-to choice for legitimate businesses for web scraping, ad verification, and market research, but the same features enable widespread abuse.
IPIDEA operated through deceptive practices that put millions of consumers at risk. The network embedded software development kits into seemingly legitimate applications, including games, utilities, and VPN services. These SDKs turned user devices into proxy exit nodes without clear disclosure and/ or informed consent.
Google's investigation revealed that IPIDEA controlled at least 13 allegedly independent proxy brands, including 360 Proxy, Luna Proxy, PIA S5 Proxy, and Cherry Proxy, creating an illusion of market diversity while maintaining centralized control.
The security implications extend beyond privacy concerns. When a device becomes an exit node, network traffic that users don't control passes through their device and home network. Research from Krebs on Security confirmed that IPIDEA proxies not only route traffic through exit nodes but also send traffic to the devices themselves, exposing security vulnerabilities to the internet. Consumers whose devices were enrolled faced potential consequences, including being flagged as suspicious by service providers, blocked from accessing websites, and experiencing compromised home network security.
The scale of criminal activity facilitated through IPIDEA was staggering. Threat actors used the network for:
- Access to victim SaaS environments and on-premises infrastructure
- Password spray attacks against corporate accounts
- Botnet command and control operations, including the BadBox2.0 botnet
- Espionage operations from state-sponsored groups
- Information warfare campaigns
The business case for ethical sourcing
Using unethically sourced IP addresses creates substantial legal and operational risks for businesses. Companies that unknowingly partner with providers operating through deceptive practices may find themselves implicated in regulatory violations, including data protection, even when their own intent was legitimate.
Data protection laws like GDPR and the California Consumer Privacy Act impose strict requirements on how businesses shall collect, transparently inform, and use personal data. When proxy providers harvest IPs and bandwidth without properly informing users and obtaining their valid consent, they create compliance vulnerabilities for every business using their services. Regulatory authorities increasingly scrutinize not just direct data practices but also the practices of third-party service providers.
The reputational damage from association with unethical providers can be severe. When news breaks that a proxy network facilitates cybercrime or exploits consumer devices, businesses using those services face difficult questions about their due diligence processes. Investors, customers, and partners expect companies to vet their technology stack thoroughly.
Security implications compound these concerns. If your proxy provider facilitates malicious actors, your business operations could be compromised through the same infrastructure. Threat intelligence shared among criminal groups often includes information about which networks and providers offer the best cover for illicit activities. Companies using these same networks may find their legitimate traffic flagged alongside criminal operations.
The financial costs of remediation after a provider takedown can be substantial. When Google disrupted IPIDEA's infrastructure, businesses relying on their services faced immediate operational disruptions. Emergency migration to new providers, investigation of potential security breaches, and communication with stakeholders all require resources that ethical sourcing would have prevented.
What ethical IP sourcing looks like
Legitimate residential proxy providers operate with fundamentally different practices than networks like IPIDEA, 360 Proxy, Luna Proxy, PIA S5 Proxy, and Cherry Proxy. Ethical sourcing requires transparent disclosures and consent mechanisms where users explicitly understand and agree to their devices being used as proxy exit nodes.
Clear disclosure stands as the foundation of ethical practice. Users must know before installation that an application will use their bandwidth and IP address for proxy services. This disclosure should appear prominently in user agreements/ terms of service documents. The specific ways the application will use network resources should be explained in accessible, clear language.
Fair compensation models demonstrate respect for users who choose to participate. Ethical providers like Decodo enable users to earn rewards through peer-to-peer networks where they voluntarily share their network traffic. This approach fosters a collaborative community while allowing participants to get rewarded for their internet resources with full transparency about how their connection is used.
Security protections for exit node users separate legitimate providers from exploitative networks. Ethical providers implement measures to:
- Prevent malicious traffic from passing through user devices
- Monitor for abuse and terminate suspicious accounts
- Provide users with control over when their devices participate
- Maintain network isolation to prevent exposure of local devices
- Ensure that only essential data for proxy pool functionality is collected
Auditable practices give businesses confidence in their provider relationships. Decodo maintains ISO/IEC 27001:2022 certification for its proxies and Scraping API products, demonstrating adherence to internationally recognized information security standards. This certification covers access management, risk assessment, infrastructure reliability, and continuous monitoring, built to scale with customer needs.
Ethical companies maintain documented proof of user consent, undergo regular security audits, and provide information about their sourcing methods. This documentation becomes crucial for demonstrating compliance during regulatory reviews. Decodo follows a unified information security framework aligned with the highest data protection standards, including adherence to globally known laws such as GDPR and CCPA, ensuring lawful and transparent data processing.
Partnership with reputable industry organizations offers another indicator of ethical operations. Decodo serves as a co-founder of the Ethical Web Data Collection Initiative (EWDCI), an international consortium focused on building trust in web data collection through clear ethical standards. EWDCI-certified providers follow core principles centered on legality, ethical data use, ecosystem engagement, and social responsibility.
Responsible customer verification demonstrates commitment to preventing misuse. Ethical providers implement layered verification approaches, including automated fraud checks, third-party anti-fraud screening, and, when needed, KYC processes. They also actively restrict access to sensitive targets such as banking platforms, government sites, streaming services, app stores, ticketing websites, and mailing services.
Choose an ethical proxy provider
115M+ ethically-sourced residential IPs from 195+ locations with a 3-day free trial.
Due diligence checklist for businesses
Vetting proxy providers requires systematic evaluation of their practices and claims. Companies should verify provider assertions of "ethical sourcing" with documented proof rather than accepting marketing statements at face value.
- Assess transparency standards. Evaluate whether the provider openly publishes information about their sourcing methods, user protections, and operational practices. Opacity often signals problematic practices. Legitimate providers maintain detailed documentation available to potential business customers.
- Investigate provider history. Research the provider's track record through industry reports, security researcher analyses, and news coverage. Check whether the provider has faced takedowns, legal challenges, or public criticism from security researchers.
- Examine security measures. Request detailed information about how the provider protects exit node users from security vulnerabilities. Understanding their technical architecture helps assess whether they prioritize user safety or simply extract value from consumer devices.
- Verify compliance certifications. Look for relevant certifications and compliance documentation. Ethical providers typically undergo regular security audits and comply with data protection regulations. The absence of such documentation should raise concerns.
- Test provider responsiveness. Identify specific questions you would like to ask to assess a particular platform's match with your business case. If the provider has all of the best practices in place, it shouldn’t be a problem to get concrete answers to your questions.
- Consider geographic sourcing. Understand where the provider sources their IP addresses and whether those regions have adequate legal protections for consumers. Providers sourcing from regions with weak consumer protection laws may operate with fewer constraints.
Bottom line
Google's disruption of IPIDEA marks a turning point for the residential proxy industry. The coordinated takedown, involving partnerships with Cloudflare, Spur, and Lumen's Black Lotus Labs, signals that the gray market thriving on consumer exploitation and cybercrime facilitation faces intensifying scrutiny from technology companies, law enforcement, and regulatory authorities. Businesses must thoroughly vet their IP sourcing partners, as the risks of partnering with unethical providers now clearly outweigh any short-term benefits.
Ethical providers like Decodo demonstrate that transparent, consent-based models are commercially viable while maintaining user trust and regulatory compliance. With ISO/IEC 27001:2022 certification, EWDCI co-founder status, and robust customer verification processes, Decodo exemplifies how residential proxies can serve legitimate business needs without exploiting consumers.
About the author

Benediktas Kazlauskas
Content Team Lead
Benediktas is a content professional with over 8 years of experience in B2C, B2B, and SaaS industries. He has worked with startups, marketing agencies, and fast-growing companies, helping brands turn complex topics into clear, useful content.
Connect with Benediktas via LinkedIn.
All information on Decodo Blog is provided on an as is basis and for informational purposes only. We make no representation and disclaim all liability with respect to your use of any information contained on Decodo Blog or any third-party websites that may belinked therein.