Error Code 1010: Causes, Solutions, And Prevention For Cloudflare Users And Website Owners
Cloudflare’s Error 1010 can be a real headache for website owners and visitors. It usually appears when its security detects something unusual or automated, even if it’s a genuine request. In this article, we'll outline what the Error 1010 code means, why it occurs, how to identify it, and the best solutions to fix and prevent it.
Justinas Tamasevicius
Last updated: Oct 03, 2025
4 min read
What is error code 1010?
Error 1010 is an error code shown when an owner, using Cloudflare, blocks some attempting visitors to their website based on the latter’s detected traffic patterns or other features.
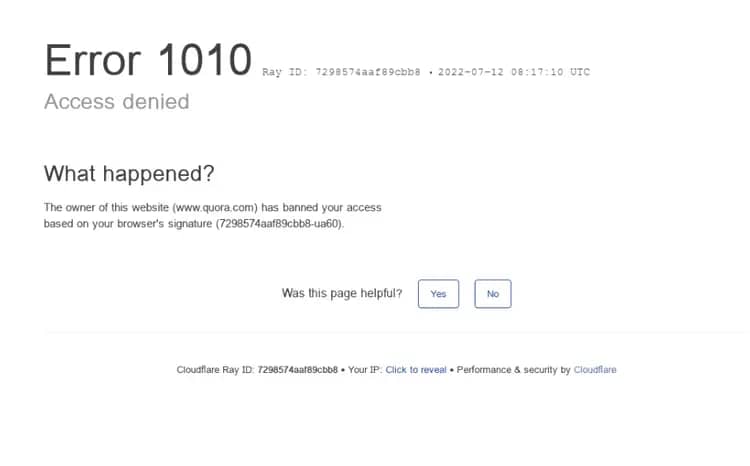
Here is how it generally appears: “Error 1010: The owner of this website has banned your access based on your browser’s signature (request header)”
Cloudflare error 1010, also known as the “Access Denied error”, occurs when Cloudflare’s browser integrity check or firewall blocks a request it perceives as suspicious.
This means that the way the browser, server, or automation tool displayed itself caused Cloudflare to reject the request.
Why does error code 1010 occur?
Error 1010 occurs when Cloudflare blocks a request it interprets as automatic or malicious.
Cloudflare typically bases this decision on browser fingerprinting and integrity checks, actively analyzing request headers, cookies, and other signals to determine whether the client is genuine.
Before a request reaches the website’s server, Cloudflare blocks it if it does not behave like a “normal” browser.
How Cloudflare detects suspicious traffic
These are the techniques Cloudflare uses to detect inorganic traffic.
- Browser fingerprinting. Cloudflare uses browser fingerprinting to identify suspicious traffic by gathering information about WebGL, time zones, screen resolution, and HTTP headers.
- Web Application Firewall (WAF). The WAF responds to visitor requests by applying both Cloudflare's default rules and rules set by the website owner. The WAF may trigger error 1010 if it notices a suspicious pattern, such as traffic from a flagged Autonomous System Number (ASN), malformed headers, or a SQL injection attack.
- TLS/JA3 Fingerprinting. Each browser negotiates SSL/TLS slightly differently. Cloudflare hashes these handshake details into a JA3 fingerprint. Cloudflare flags the request and generates an error 1010 code if the fingerprint matches a known curl or bot, or if it differs from those of popular browsers.
- Request pattern analysis. Cloudflare tracks the frequency and timing of requests made to its services. Because bots are known to send identical requests quickly and without human-like pauses, Cloudflare flags them.
- Header and cookie validation. Real browsers generate and preserve cookies, such as the “cf_clearance” cookie. Bots or stripped-down browsers often ignore these cookies, causing Cloudflare to block them.
- Automated tools and bots. One of the primary causes of this error is the use of automated tools and bots. Automated tools, such as Puppeteer, Selenium, bot crawlers, and scraping tools, frequently generate requests that differ from those a typical browser would produce. Patterns like request timing, header completeness, TLS fingerprints, and mouse or keyboard simulations also vary between them. It marks a request as suspicious and raises error 1010 when it significantly deviates from what a typical browser would generate.
- Browser plugins and extensions. Plugins or extensions that alter requests may also be the source of the problem. Specific extensions, such as privacy tools or ad blockers, may disrupt the transmission of web traffic. A browser plugin may delete cookies, prevent necessary JavaScript code from executing, or even inject various headers. This appears unusual to Cloudflare's system because a legitimate browser session should maintain a certain degree of uniformity in headers and cookie behavior. Because of this, even legitimate users may receive a 1010 error just because their request appeared to be bot-like due to a browser plugin.
- Malfunctioning security software. This error is also frequently caused by local security tools, such as firewalls, VPN clients, and antivirus software. Occasionally, these programs alter web traffic in a way that compromises request integrity. For example, a VPN might direct traffic through an IP range that Cloudflare links to malicious activity or proxies. Cloudflare's WAF actively compares each request to expected norms so that these modifications may flag legitimate traffic as harmful and trigger Error 1010.
- Unusual HTTP requests. Submitting incomplete HTTP requests is another frequent reason. Cloudflare expects browsers to include specific headers, such as “User-Agent” and “Accept-Language”, and it expects cookies to follow a particular formatting. If a request lacks these elements, does not adhere to specific formatting guidelines, or maliciously presents these headers, it triggers the error. This can also happen when programmers create scripts that communicate with an endpoint without precisely mimicking how a real browser would behave.
Diagnosing error 1010
When Cloudflare displays an the infamous "Error 1010: Access Denied" page, the first challenge is actively determining whether your browser environment, the website's firewall rules, or an automated process triggered the block.
Correct diagnosis is essential because the right solution depends entirely on what triggered the error in the first place. Cloudflare usually displays error 1010 with the message:
“Access denied. What happened? The owner of this website has banned you temporarily from accessing this site.”
When diagnosing the error, it helps to gather details about the context in which it appeared. Some of the most valuable pieces of information include:
- The exact error message and your unique Ray ID allow website administrators to trace the blocked request.
- The browser you used, whether you were in normal mode or incognito, and if any extensions were active.
- Your network setup might trigger those errors. Check whether you're connected to a VPN, route your traffic through low-quality proxies, or use a corporate network that alters your original IP address.
- Your recent activity might also cause some suspicion. If you just refreshed the page a few times, scrolled and clicked through the website back and forth, the anti-bot mechanisms might think that you're not a legit user but rather a bot.
These components are crucial hints to help you diagnose the error.
Another critical step in diagnosing error 1010 is determining whether Cloudflare flagged you as a legitimate user or an automated, suspicious actor.
Browser extensions, aggressive privacy tools, VPNs with bad IP reputations, or incorrectly configured firewall rules on the website are usually the causes of the error for legitimate users. In these situations, the site administrator can restore access by making small changes on the user's end.
On the other hand, Cloudflare blocks automated tools and bots when it notices odd request patterns. Some examples include high-frequency traffic, missing headers, or signatures connected to Selenium or Puppeteer tools.
Get the Latest AI News, Features, and Deals First
Get updates that matter – product releases, special offers, great reads, and early access to new features delivered right to your inbox.
How to fix error code 1010 as a user
There are several steps you can take to restore access as a user after encountering the error code 1010. These range from basic troubleshooting to advanced adjustments, depending on whether you are a casual browser or someone running automation scripts.
Refresh the page
Sometimes, the error occurs because of a temporary misidentification. Actively refresh the page or wait a few minutes before retrying. This can resolve the issue, especially if Cloudflare flagged your request during a brief traffic surge.
If a short spike in traffic triggered the error, the refresh helps you to bypass it without further investigation.
However, if refreshing the page doesn’t work after several trials, then the problem might lie deeper in your browser setup.
Disable browser extensions
Extensions like ad-blockers, privacy tools, or script managers can alter your request headers or block JavaScript execution, which Cloudflare uses to verify that visitors are human.
Try turning off these extensions and reloading the page. Testing in an incognito window or a clean profile without add-ons is a quick way to confirm if these extensions are the culprit.
Once identified, you can disable or configure the specific extension so it does not interfere again.
Turn off VPN or proxy services
Many VPN providers use shared IP addresses, and if one person misuses that IP, everyone routed through it inherits the “bad reputation”.
When you disable the VPN, your traffic comes directly from your ISP, making it easier for Cloudflare to recognize you as a legitimate user.
If you must continue using a VPN, try a different server location or switch to one that offers a residential IP address.
Change browsers or devices
If the problem persists, try visiting the website using a different device or browser. This step helps you determine whether the issue is with your network connection or your browser configuration.
Switching browsers also helps determine whether a specific browser build, a corrupted profile, or an extension unique to that environment is the cause of the error.
Testing from a completely different device on the same network helps to differentiate between client fingerprint issues and network/IP reputation issues.
Clear cookies and caches
Outdated or corrupted cookies may interfere with Cloudflare’s integrity checks. A fresh session, which frequently avoids cached errors, is ensured by clearing the cache and cookies in your browser.
Clearing cookies forces Cloudflare to issue new tokens and session data, which resolves persistent blocking. It also removes any corrupted cache entries that could confuse the validation process.
After completing this step, always restart your browser before attempting to reload the site.
If you're running an automated tool for testing or scraping, basic troubleshooting won’t be enough. Cloudflare error 1010 occurs because the system recognizes your traffic as non-human.
To avoid being blocked, you may need to adjust your automation environment to simulate real browsers more effectively.
Run JavaScript in headless browsers
Tools like Selenium and Puppeteer often get detected when they fail to execute or respond to JavaScript challenges.
Running your scripts with full JavaScript support, instead of skipping it, increases the chances of passing Cloudflare’s checks. This is because Cloudflare relies on script-based challenges to verify human behaviour.
If your automation skips or fails these, it stands out as bot-like activity. Enabling JavaScript execution makes your requests appear closer to those of a real user.
Rotate headers and user agents
Static and incomplete headers are a clear giveaway for bot activity. Ensure your requests include standard headers such as User-Agent, Accept-Language, and cookies.
When every request appears identical, Cloudflare flags the repetition as suspicious. By intelligently rotating headers and user agents, you create a variation that mimics the behavior of normal human browsing.
Ensure that the headers remain consistent with each other so they appear as authentic as possible.
Use undetectable browser automation tools
Specialized automation frameworks, such as Playwright Stealth or Puppeteer Extra Stealth, help mask the fact that a browser is automated.
It achieves this by patching browser fingerprints, removing properties such as webdriver, and more accurately mimicking human interaction.
This makes it harder for Cloudflare’s checks to distinguish between your tool and a genuine user session.
Use residential or ISP proxies
Cloudflare frequently flags data center proxies because attackers and scrapers commonly use them.
Residential proxies give your traffic the appearance of an everyday user, which reduces the risk of being automatically blocked. They also help distribute requests across different IP addresses, avoiding the concentration that often raises red flags.
Switching to residential proxies that route traffic through legitimate consumer ISPs can dramatically reduce detection.
If you're working with websites that have advanced anti-bot mechanisms, consider choosing static residential (ISP) proxies that have the residential proxy authenticity and datacenter speeds.
Try residential proxies for free
Bypass CAPTCHAs, IP blocks, and geo-restrictions with high-quality residential proxies.
How to fix error code 1010 as a website administrator
As a web administrator, fixing these errors is less about turning off protections outright and more about calibrating your security rules. This makes it easier for Cloudflare to distinguish between harmful and legitimate activity effectively.
Examine your Cloudflare security settings
Many false positives stem from the Web Application Firewall of the Browser Integrity Check, both of which check incoming requests.
When tuned aggressively, they can treat normal users as suspicious, especially if they browse with VPNs, privacy extensions, or non-standard headers.
You can reduce unnecessary blocking without exposing your website by temporarily disabling the Browser Integrity check or lowering the overall security of the Cloudflare dashboard.
Allow known safe traffic
Allowing known safe traffic is another popular solution. Allow specific IP addresses or geographical areas to bypass restrictions if you frequently notice them being blocked.
For example, Cloudflare may flag a business partner's corporate network or a reliable uptime monitoring bot simply because their request patterns appear automated.
Essential services are kept out of the same network as bad actors by whitelisting those IP addresses or user-agent strings.
Cross-check firewall and rate-limiting rules
It is also important to cross-check your firewall rules. Over time, the website accumulates custom rules for malicious users.
However, these rules can become outdated or overly broad. A country-wide block, for instance, may unintentionally lock out genuine users travelling abroad.
Similarly, strict rate-limiting rules may frustrate individuals with unstable connections or those who frequently refresh a page. You can reduce needless restrictions while maintaining strong protection by reviewing and updating these rules with new information.
However, balance is the most important thing. While overly strict security can irritate your users, inadequate security leaves your website vulnerable to misuse or even hacking.
Administrators should regularly monitor traffic analytics in their Cloudflare dashboard to identify spike patterns or false positives.
Preventing error 1010 in the future
Preventing the error from happening again depends on who you are.
Whether you're a website owner responsible for managing Cloudflare’s defenses, an end-user simply trying to browse the web, or a developer running automated tools.
For regular users, prevention is relatively more straightforward. It often comes down to:
- Maintaining a stable and transparent browsing environment
- Using mainstream browsers without aggressive extensions
- Keeping cookies enabled
- Avoiding suspicious VPNs or poor quality proxy services
- Keeping your browser and operating system up to date
For web admins, prevention is usually about:
- Regularly reviewing firewall rules
- Monitoring analytics
- Fine-tuning bot management settings all contribute to improved usability
- Establishing a process for handling reports from users who encounter the 1010 error.
Technical users and developers who rely on automation need a different strategy, though. The key here is to ensure that scripts and scraping tools mimic real browser traffic as closely as possible.
Hence, it's essential to run JavaScript where necessary, send complete and standard headers, and rotate user agents to prevent repetitive patterns. Using residential ISP-backed proxies instead of data center proxies provides an additional layer of legitimacy.
For those who need to scrape at scale, using specialized scraping APIs or stealth automation frameworks reduces the chance of repeatedly triggering Cloudflare’s protective filters.
Bottom line
Cloudflare’s error 1010 can be frustrating. However, it exists to protect websites from malicious users or traffic.
Ultimately, end users can resolve this error through simple troubleshooting, while developers must refine their automation to send more human-like requests. Administrators, on the other hand, should monitor that security measures block real threats without affecting legitimate users.
By following best practices and staying mindful of how Cloudflare detects anomalies, error 1010 can shift from a persistent roadblock to a manageable exception.
High-quality residential proxies
Collect real-time data, run market research, and manage multiple accounts without blocks – test residential proxies with a 3-day free trial.
About the author

Justinas Tamasevicius
Head of Engineering
Justinas Tamaševičius is Head of Engineering with over two decades of expertize in software development. What started as a self-taught passion during his school years has evolved into a distinguished career spanning backend engineering, system architecture, and infrastructure development.
Connect with Justinas via LinkedIn.
All information on Decodo Blog is provided on an as is basis and for informational purposes only. We make no representation and disclaim all liability with respect to your use of any information contained on Decodo Blog or any third-party websites that may belinked therein.